
ContentsAbout This Chapter Account Access Security Maintenance TCL Command Security TCL Command Aliases File Access Verbs File Security |
In this chapter we will discuss the Security of your System. Often the best systems are those where there has been direct user input into the development of the applications that make up the entire system. Wizard gives the System Administrator the ability to let end users develop or change Screens and Reports by restricting access to processes, files, TCL, Verbs, etc. This means with a minimal amount of training users can assist in the development of your system.
The Security menu in the Wizard account contains two options which allow you to restrict users' access to the account or other Wizard accounts on the system. The two options are:
Both these options present you with a Wizard screen The screen looks like this:

There are two fields on the screen, the first allows you to enter a list of ports which you want to restrict from using the accounts.
To restrict ports, you type the port numbers separated by commas. If you want a range of ports, you can type, for example, 1-10 which is equivalent to typing:
1,2,3,4,5,6,7,8,9,10
If you already have a series of ports restricted which you want to adjust, you could go to this field and type, for example:
A20,21,30-35
which will add ports 20, 21, 30, 31, 32, 33, 34, and 35 to the current list.
Alternatively, you may want to delete some of the ports from the list. In this case you may type (for example):
D5-10,13
which will delete the port numbers 5, 6, 7, 8, 9, 10, and 13 from the current list.
Note that port zero (0) cannot be put on this list. Access to Wizard cannot be restricted from that port.
The other field on this screen is a line item set which allows you to enter a message which is displayed to the port which is restricted from logging on when it tries to log on.
The Security Maintenance screen allows you to set or amend security levels for individual items within Wizard. You can use this so that a particular item in a file may not be read by a user with a security level below that which you specify for the item.
When you go into this option, the following screen is displayed:
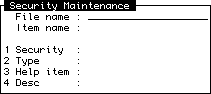
The fields on this screen are then as follows:
| B | Basic source code. |
| C | Program catalogue pointer. |
| F | File (not relevant in this screen). |
| M | Wizard Menu. |
| P | PICK PQ-type proc. |
| R | Wizard PROC report. |
| S | A Wizard S type subroutine. |
| V | A verb (file is MD). |
| W | A Wizard screen |
| X | Miscellaneous (any other type). |
WIZHELP,USER.MENU
If no security item exists for a particular item, Wizard assumes that it has a security level of 0.
Wizard offers an enhanced TCL environment for the user which has the benefit of added security control. This, and the remainder of screens on the Account Security menu, are related directly to setting up the security environment for TCL within Wizard.
This screen allows you to assign a security level to TCL commands. When assigned a security level, Wizard will check whether the user has sufficient security clearance to use that command before executing. If the user's security clearance is inadequate, a suitable message will be given.
The screen looks like this:
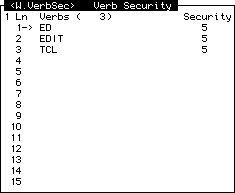
Use of the screen is quite simple. All you need to do is move to a blank line in the Line Item Set (or create one by typing /E on any line), enter the TCL command you want to set with a security level, and (after pressing
Thus, for example, you may wish to give the TCL command CREATE-FILE a security level of 8. This can be done for any command valid from TCL.
To delete a command from this list, move to its line and type /D. Then file the item when you have finished.
TCL commands may be given an alias by using this screen. An alias is an alternative name for a command, so for example if I create an alias of CF for the command CLEAR-FILE, when I want to clear a file I need only type in the command CF.
Alias commands are useful for two main reasons:
The Alias screen looks like this:
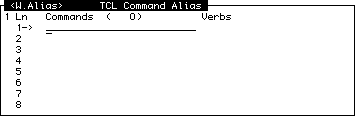
To enter a command alias, you go to a free line in this screen's Line Item Set (or make a new line using the /E command , and then under the field labelled Command you type your alias (say CF for example) and press
You should now be positioned under the Verb label. Here you type in the name of the TCL command you are creating an alias for (say CLEAR-FILE).
When you file the item, the alias will be made to take effect. For users already in TCL when you file the changes, the change will not be effective until they have logged off or returned to the menus.
This screen simply contains a list of TCL verbs which access files. The list is necessary because, whenever Wizard finds that a user has typed one of these commands it checks to see if the file's security (see the next screen on this menu) will allow this user access.
The screen looks like this:
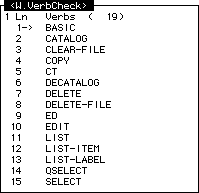
If you want to add any more commands to the list, you need only move to a blank line in the Line Item Set (or create a blank line by typing /E) and enter the command which accesses files.
Wizard will assume that a file command takes the format
[Command] [File Name]
when it looks to see which file you are trying to access. Thus it will only function for TCL commands which take this format.
File Security is covered in Chapter 6, Wizard File Maintenance.